Stéphanie Ouillon, irc: arroway stephouillon@mozilla.com



 http://bgr.com
http://bgr.com



{
"name": "My App",
"description": "My elevator pitch goes here",
"launch_path": "/",
"icons": { "128": "/img/icon-128.png" },
"developer": {
"name": "Your name or organization",
"url": "http://your-homepage-here.org"
}
}
Présentation par Julien Wajsberg et Jérémie Patonnier
 commons.wikimedia.org
commons.wikimedia.org
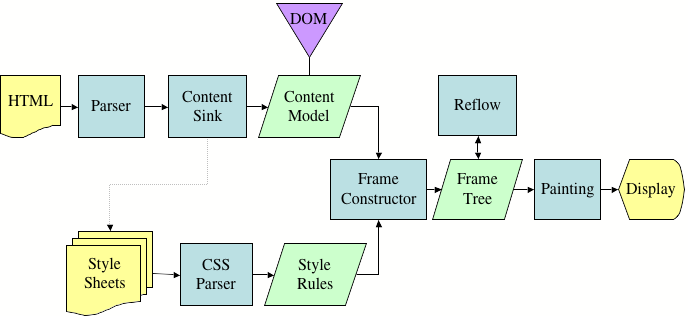 MDN
MDN




 https://securityreactions.tumblr.com
https://securityreactions.tumblr.com